Recently, reports have emerged of hackers impersonating IT support on Microsoft Teams to trick users into downloading malware. This deceptive approach highlights the evolving tactics cybercriminals are using to exploit communication tools we rely on daily.
At Third Octet, your security is our top priority. We want to make sure you’re equipped to recognize and handle any suspicious interactions. Here’s what you should know and how to stay safe.
The Threat: Hackers Impersonating IT Support
Cybercriminals are using fake IT support identities to infiltrate organizations. By sending messages through Microsoft Teams, these attackers often claim to need your help resolving an issue, like downloading an urgent update. Once the user complies, malware is installed, potentially giving attackers access to sensitive company information.
How We Communicate with You
At Third Octet, we take extra precautions to ensure our communication is secure and trustworthy. Here’s how you can tell it’s really us:
- Official Channels Only: Our IT support team will always use designated communication methods, such as emails from official @thirdoctet.com addresses, direct phone calls, or messages sent through our Customer Portal at portal.thirdoctet.com. We do not reach out via Teams unless it’s explicitly part of our agreed support process or if we have previously engaged with you via Teams Chat (in which case, you likely have the existing chat history still within Teams).
- Personalized Information: Our messages will include specific details related to your account, such as your name and known project information. We never send generic or vague messages.
- Clear Instructions and Verification Steps: If we ask you to take an action, such as downloading software or making a configuration change, our team will always provide clear instructions and a way to confirm the request’s legitimacy.
What to Do When You Receive a Message from Outside Your Organization
When someone outside your organization sends you a Microsoft Teams message, you may see a prompt similar to the one shown below:
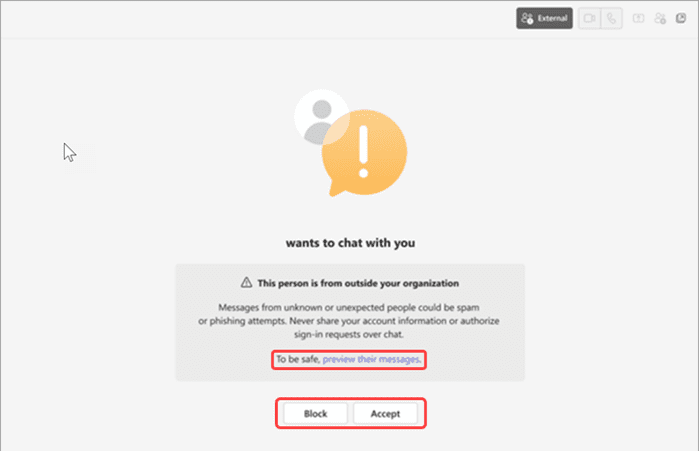
This prompt will alert you that the person is external to your organization. Here are your options:
- Preview Their Messages: You can select “preview their messages” to see what the sender is attempting to communicate before engaging.
- Block: If the message seems suspicious or comes from an untrusted source, use the “Block” option to prevent further communication.
- Accept: Only accept the message if you are confident about the sender’s identity and legitimacy.
Important Reminder: If you receive an odd or unexpected message, do not engage. Instead, call us directly at 647-728-0610 for verification.
How to Verify a Communication from Us
We understand that security is only as strong as the weakest link, and we want to make it easy for you to verify our communications. Here’s what you can do:
- Check the Source: Always double-check the email address or phone number. If something feels off, call us directly at 647-728-0610 to confirm the authenticity of the request.
- Use a Secondary Method: If you receive a suspicious message through one medium (like Teams), use another method (like email or a phone call) to confirm the communication with our team.
Reporting Suspicious Activity
If you ever receive a message or call that you think might be a phishing attempt or a scam, don’t engage. Instead:
- Contact Us Directly: Call us at 647-728-0610, use our Customer Portal at portal.thirdoctet.com, or email us to report the incident.
- Stay Alert: Forward the suspicious message to our security team for analysis.
- Avoid Clicking Links: Don’t click any links or download attachments from unverified sources.
Your Security Matters to Us
At Third Octet, we are constantly evolving our security measures to counter threats like these. Staying informed is one of the best defenses against cybercrime, and we are here to support you every step of the way.
Stay vigilant, stay secure, and don’t hesitate to reach out if you have any questions or concerns about your IT safety.




0 Comments