It’s never a good time to let your guard down.
In the whirlwind of running a small business, IT security can easily slip through the cracks. Consider us your reliable lighthouse, guiding you to the safety of robust cybersecurity.
Complete our five-minute assessment and join other Burlington Chamber members in strengthening your IT defenses.

%
of reported cyber incidents in Canada impact SMB.
With cyber threats escalating, no business, big or small, is immune to the risks.
Small businesses are not just operationally unique but also uniquely vulnerable. The rise in cyber attacks highlights the critical need for robust cybersecurity measures. It’s not just about protecting data; it’s about safeguarding your business’s future, reputation, and the trust of your customers. Today, more than ever, effective IT security is a cornerstone of business resilience and success.
Participating in our five-minute assessment will give you invaluable insights into your cybersecurity stance, aligning your business with the proactive approach of fellow Burlington Chamber members. This isn’t just an assessment; it’s a step towards empowering your business against the ever-evolving cyber threats.
Your Path to Enhanced Cybersecurity
Submit your Assessment
Begin by sharing insights about your current IT infrastructure through our comprehensive assessment.
Analysis of Your Results
Our team of experts will meticulously analyze your responses to gauge your cybersecurity stance.
Customized Report
Within 3 business days, receive a personalized report with your cybersecurity score and recommendations to boost cybersecurity readiness.
Expert Guidance
If you need guidance on the next steps, we’re here to help cover any gaps and strategize for a robust cybersecurity framework.
Begin assessment.
Please answer these questions to the best of your knowledge. Your honest responses will lead to recommendations for better cybersecurity for your business in 2024.
While you wait…
Why Roadmaps Are Essential for Clear IT Leadership
Discover how implementing strategic IT roadmaps provides clarity, accountability, and freedom from daily firefighting. Regain control and refocus your leadership with structured visibility.
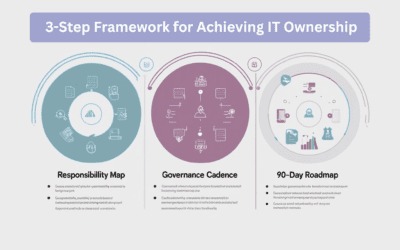
Who Really Owns IT? (Hint: It Can’t Keep Being You)
Stop being the fallback for every tech issue. Discover a 3-step framework to assign IT ownership, minimize downtime, and regain your strategic focus.
The Power of Letting Go: How SMB Leaders Can Step Back from IT Without Losing Control
This article is for SMB owners who want to step back from day-to-day tech headaches without losing visibility or control.
Hackers Are Posing as IT Support on Microsoft Teams: What You Need to Know
Hackers are impersonating IT support on Microsoft Teams to spread malware. Learn how to identify and verify legitimate communication from Third Octet and keep your organization secure.
Unlocking Productivity with ChatGPT
Unlock productivity with ChatGPT and Microsoft Copilot. Explore how Third Octet leverages AI for efficiency, data security, and ethical use, along with practical tips to maximize AI in your daily tasks.