
Challenge #2
Combat MFA Fatigue with Microsoft Authenticator
Enhance security and maintain your team’s efficiency by configuring Microsoft Authenticator to minimize Multi-Factor Authentication (MFA) fatigue.

Why?
Multi-Factor Authentication (MFA) is a cornerstone of modern cybersecurity, especially in Microsoft 365, but its frequent prompts can lead to what’s known as MFA fatigue. This occurs when users, overwhelmed by constant verification requests, become less cautious and might inadvertently approve unauthorized access. Microsoft Authenticator tackles this challenge head-on, offering enhanced features that strike a balance between security rigor and user convenience.
Think of logging into your systems like opening a high-tech, secure door. Normally, MFA acts like a double-check, asking you ‘Are you really the key owner?’ But if this question is asked too often, it can become annoying, leading to carelessness. That’s where the updated Microsoft Authenticator comes into play, making this double-check both smarter and easier.
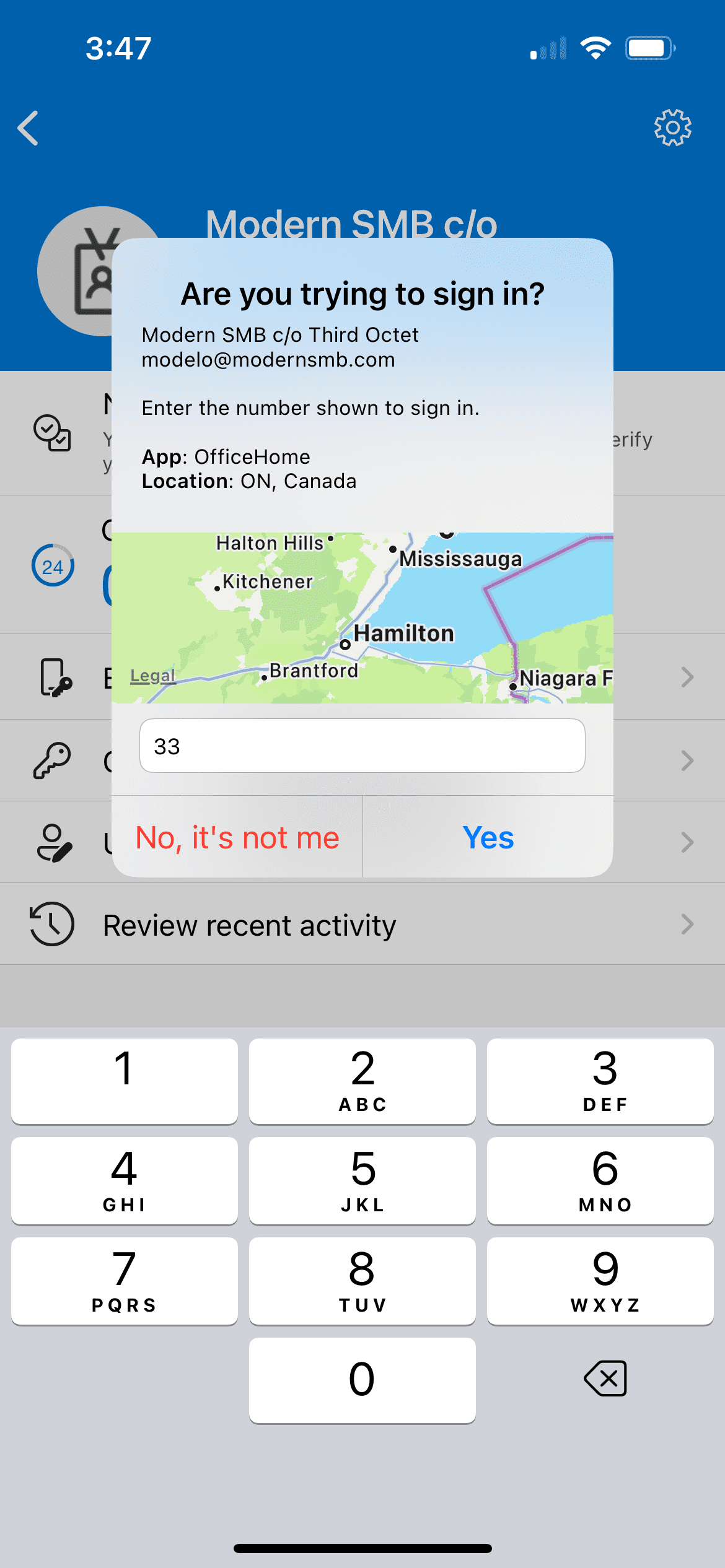
Picture this: each time a login attempt is made, Microsoft Authenticator now shows not just a prompt but also helpful details – like where the request is coming from (geographic location) and which app is asking for it (application name). It’s like your digital security guard telling you, ‘Someone at the front door with your key claims to be from the office’ – you’d instantly know if it’s expected or not.
Plus, there’s a new twist – number matching. When you try to log in, the app shows a number on your phone and asks you to type that same number on your computer. It’s like a secret handshake – only the real you, holding your phone, would know the right number to enter.
By adding these smart features, we’re not just asking ‘Is this you?’ but giving you the clues to answer confidently. This reduces the chance of letting in someone pretending to be you and keeps your digital doors securely locked.
How?
We hope you’re already utilizing multi-factor authentication in Microsoft 365. If not, you may want to fast forward to our future challenge about enabling MFA for users and administrators (or come back to this challenge after you’ve done so).
Configuring Microsoft Authenticator to reduce MFA fatigue involves a few straightforward steps. Before you start, ensure you have administrative access to the Microsoft Entra admin center. Here’s how to set it up:
Step 1: Go to the Entra Admin Center
On your computer, launch a new browser window (Edge, Chrome), and type in https://entra.microsoft.com/ and press enter.
Note: You will require Microsoft 365 administrative credentials – be sure to have the username and password ready.
Step 2: Adjust Authentication Methods
Within the Microsoft Entra Admin Center:
- Look for and select Protection along the left-hand side menu
- Under Protection, look for and select Authentication Methods
- Then select Policies
Step 3: Configure Microsoft Authenticator
- Within the Policies window, under Method, find Microsoft Authenticator
- Make sure under the Enabled column, it’s set to Yes (if not, we need to get this enabled ASAP)
- Now, click Microsoft Authenticator
Step 4: Enable Advanced Features
- Within Microsoft Authenticator, select the Configure tab
- Activate the desired features, including:
- Require number matching for push notifications
- Show application name in push and passwordless notifications
- Show geographic location in push and passwordless notifications
- Note, there are two important options:
- Microsoft managed: This option allows Microsoft to manage whether this feature is enabled or disabled.
- Enabled: This option forces the particular setting to always be on, which is our preferred route as it maintains familiarity for your staff.
- Once you are satisfied, click Save.
While you’re here…
Unlocking Hidden Power: The Key Role of Training in Maximizing Your Tech Investments
Imagine investing in a state-of-the-art kitchen and only using the microwave. Absurd, right? Yet, businesses do this with technologies like Microsoft 365, missing out on powerful features due to lack of training. According to Gartner, Shadow IT can consume 30-40% of IT spending, increasing inefficiencies and risks. At Third Octet, our training programs ensure your team fully leverages these tools, unlocking their true potential. Ready to transform your technology use?
Navigating Technology Investments for SMBs
SMBs often find themselves caught between having too little technology, leading to reliance on manual processes, or too much, resulting in costly overlaps and inefficiencies. Navigating this complex environment requires a strategic approach to technology investments. Whether looking to optimize your current technology or plan for future investments, this guide offers practical insights and strategies for SMBs.
Why Switch Your Managed Services Provider?
Are you confident your current MSP is equipped to handle tomorrow’s challenges? Many businesses hesitate to switch MSPs due to fears of disruption and data security risks. At Third Octet, we ensure a smooth transition that enhances your operational success. Our proactive approach can transform your IT infrastructure, making your business more secure and efficient. Discover how partnering with Third Octet can drive your business forward.


