A story of shared hosting, broken assumptions, and the ‘blind spot’ in co-managed accountability
Before you read
This article isn’t about blame or scare tactics. It’s about how co-managed IT can quietly break down, how ransomware actually spreads, and what practical recovery looks like when responsibilities are clear and platforms are modern.
If you run an SMB with shared IT responsibility, this story is for you.
Introduction
Co-managed IT is supposed to be a strength multiplier.
Two teams. Shared responsibilities. Clear outcomes.
When it works, internal IT gets the support it needs, and the business gets resilience without disruption.
But when responsibilities aren’t explicitly defined, when legacy infrastructure is left untouched, and when assumptions take the place of standards, co-managed IT can introduce a different kind of risk. Quiet. Structural. Easy to miss.
This is the story of one such blind spot.
It’s also the story of what actually brought an SMB back to revenue in five business days, and the choices that materially reduced their risk afterward.
The warning signs no one saw coming
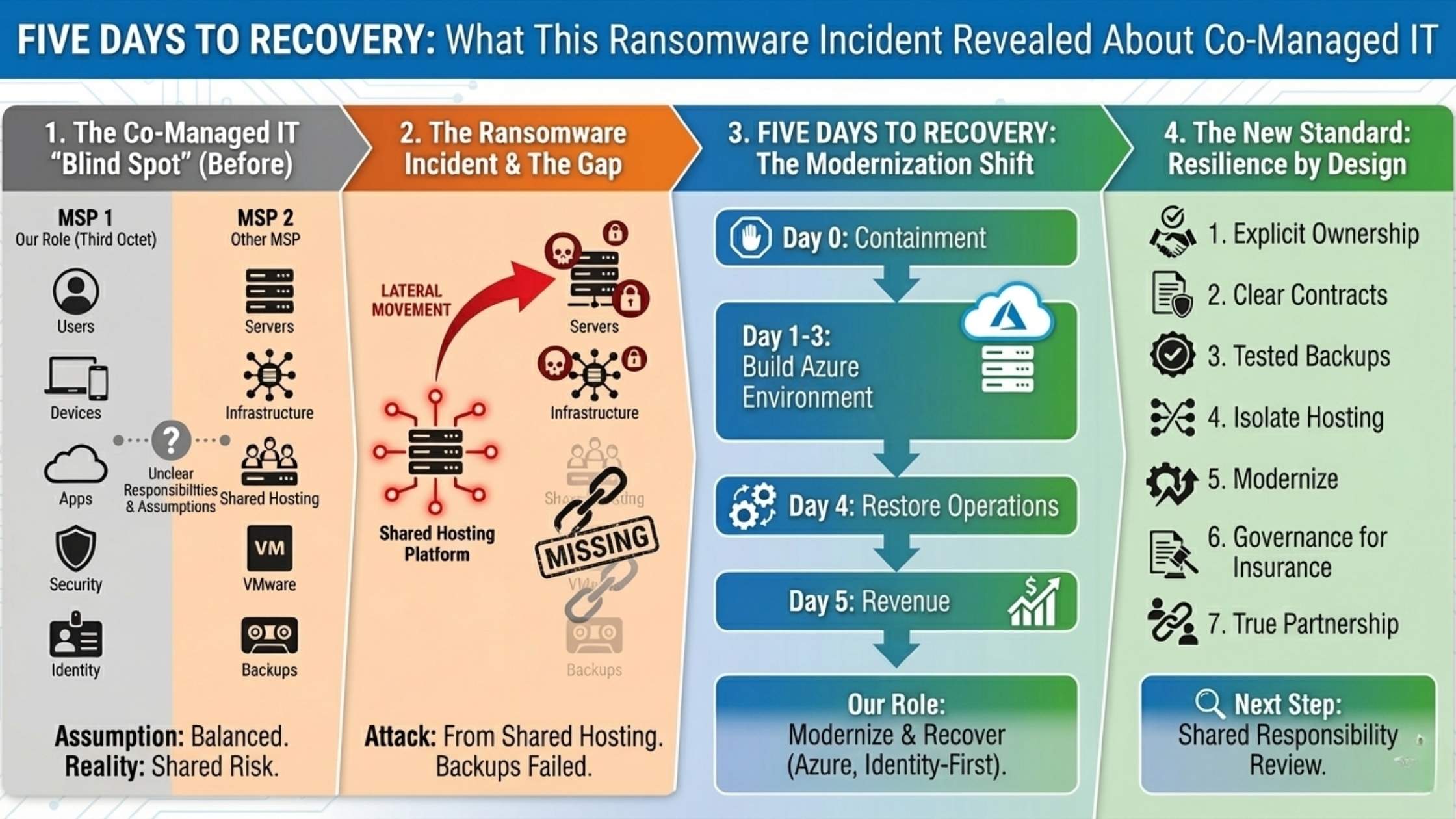
This customer had what many SMBs would consider a balanced co-managed model:
- Third Octet supported end users
- We managed devices and applications
- We secured identities and productivity platforms
- Another MSP controlled the servers, infrastructure, hosting, VMware environment, and backups
In other words:
Two MSPs. Two domains. One shared outcome.
Everything was documented. Sort of.
Responsibilities existed. Mostly.
Backups were in place. We all assumed.
On paper, it worked.
Until it didn’t.
If this sounds familiar, pause here:
You may be exposed to similar risks if:
- One provider manages users and identity while another manages servers and backups,
- backups exist, but you haven’t personally seen a restore test,
- hosting is shared with other companies you don’t know, or
- you’re not sure who rebuilds what if infrastructure disappears tomorrow.
None of this implies failure.
It usually means responsibility isn’t as clear as it should be.
For guidance on how to evaluate MSPs and avoid these gaps, bookmark MSP Buyer’s Guide: How to Choose the Right IT Partner.
The attack
The ransomware didn’t come from an employee clicking a bad link.
It didn’t come through Microsoft 365.
It didn’t come from an unmanaged laptop.
It came from the hosting platform, which was owned, operated, and secured by the other MSP.
Their hosting model relied on shared services. Shared hypervisors. Shared storage. Shared networking. A design that once seemed cost-effective, but now introduces a simple reality.
When infrastructure is shared, risk is shared.
One tenant was compromised. The ransomware moved laterally. Multiple customers were impacted, including this one.
The backups that were supposed to be there?
Some were outdated.
Some were incomplete.
Some were missing entirely.
The other MSP was overwhelmed. This wasn’t a minor incident. It was multi-tenant, fast-moving, and disruptive.
The customer was stuck.
Where we stepped in
Because we supported users and applications, we understood the business. Workflows, dependencies, and revenue-critical systems.
We couldn’t rely on the compromised platform.
We couldn’t rebuild on infrastructure that might still be infected.
And we couldn’t wait.
Our role wasn’t to replace internal IT or assign blame. It was to take ownership of recovery, restore operations, and leave the organization stronger than before.
In five business days, we:
- contained the incident,
- built a clean, secure environment in Microsoft Azure,
- recovered and rebuilt core systems,
- re-established operations, and
- returned the business to revenue generation.
Five days. Not because of heroics, but because the foundations were already modern and responsibilities were clear where they mattered.
Azure didn’t eliminate risk.
It materially reduced the risk surface by removing shared infrastructure, enforcing identity-first access, and rebuilding on isolated, monitored systems.
The result was a platform designed for today’s threat landscape (not yesterday’s).
After recovery: How internal IT fits in
Internal IT remained central after recovery.
Identity ownership, application decisions, and day-to-day operations stayed collaborative. Our role was to modernize the foundation, not remove the people who understand the business best.
Resilience improved without sidelining internal expertise.
The role of cyber insurance
Another critical factor: cyber insurance.
The policy helped cover lost revenue.
It supported recovery work.
It helped manage incident response.
This is what cyber insurance is designed for, when governance, controls, and documentation align with insurer expectations.
Increasingly, insurers expect:
- Zero-trust identity design,
- MFA everywhere,
- verified and tested backups,
- endpoint protection,
- logging and monitoring, and
- clear ownership of responsibilities.
This customer had an MSP aligned with those expectations.
The claims process worked.
Seven lessons every SMB should take from this incident
No fear-mongering. Just clarity.
- Co-managed IT requires explicit ownership
Ambiguity is a vulnerability. Every control needs a named owner. - Contracts are protection, not red tape
If responsibilities, standards, and exit terms aren’t written down, they’re assumptions. - Backups only matter if they’re tested
A backup is real only if it’s current, restorable, and verified. - Shared hosting means shared risk
Modern environments demand isolation, segmentation, and identity-first access. - Modernization reduces risk exposure
Cloud-native platforms enable patching, monitoring, and recovery by design. - Cyber insurance depends on governance
Controls, documentation, and validation determine whether claims succeed. - Choose partners who can actually partner
When alignment breaks down, the business absorbs the risk.
The bigger message: resilience is a standard of care
This customer didn’t choose ransomware.
They didn’t choose shared risk or outdated hosting.
But they did choose what came next.
They chose clarity.
They chose modernization.
They chose clearly defined responsibilities.
The result was five days to revenue restoration.
Resilience isn’t accidental.
It’s designed, governed, and maintained.
And in 2026, it’s the standard SMBs should expect, not a bonus.
A practical next step
If your environment is co-managed or split across multiple providers, clarity matters more than intentions.
We offer a 60-minute Shared Responsibility Review to help organizations answer a straightforward question:
If our primary infrastructure disappeared tomorrow, who would rebuild what, and where?
In this session, we map ownership across identity, backups, infrastructure, and recovery. You leave with a clear responsibility map you can keep, even if we never work together.
This is most useful for organizations with internal IT or multiple MSPs.



0 Comments